Changing SMB Port in Windows Server 2025 and Windows 11
Windows 11 and Windows Server 2025 improve the SMB protocol with a particular focus on security. One of the key features is the ability to switch ports to TCP 445, which offers more security and flexibility. However, this capability is limited to the server-side QUIC protocol. For decades, Windows SMB has been limited to TCP port 445, which limited the use of other ports. However, this has changed in recent versions of operating systems. Using an alternative port increases protection against opportunistic scans and strengthens security, along with measures such as signing SMB traffic and encrypting it. This change also gives network administrators more flexibility, especially when SMB traffic passes through a firewall or load balancer.
Configuring Alternative Ports for SMB Client
On the client side, you can define an alternate port for each transport mechanism (TCP, RDMA, and QUIC). The default ports for TCP and RDMA are port 445 TCP (although RDMA doesn’t require it to transmit actual data), while SMB on QUIC uses port UDP 443. You can change the default port using PowerShell, net.exe, or Group Policy.
Powershell
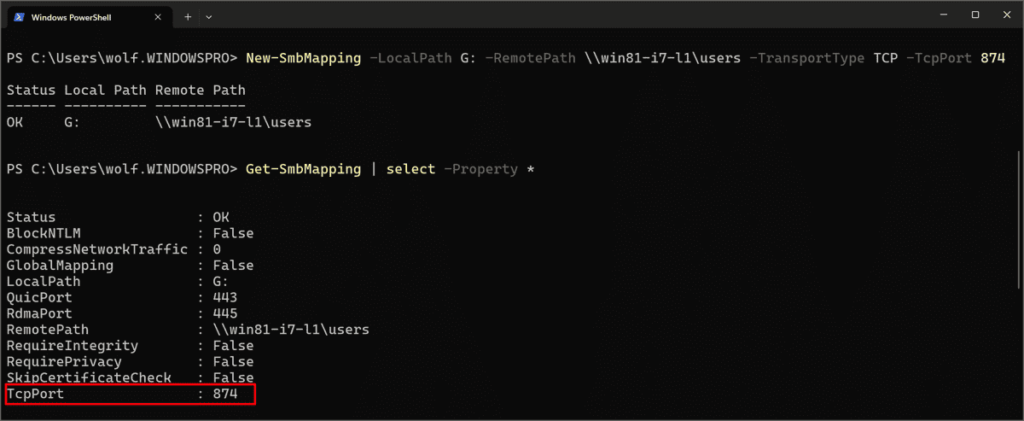
Microsoft has upgraded the New-SmbMapping command in PowerShell and added the TcpPort, RdmaPort, and QuicPort parameters. You can specify the port number between 0 and 65536. A sample command for mapping the network drive would look like this:
New-SmbMapping -LocalPath J -RemotePath \\filer.contoso.com\ppt -TcpPort 487
In this example, the ppt network subscription in filer.contoso.com will be relegated to the local J drive, and the SMB connection will use TCP port 487.
Using net.exe
The equivalent command using net.exe looks like this:
NET USE J: \\filer.contoso.com\ppt /TCPPORT:487
In both cases, you can replace TcpPort with RdmaPort or QuicPort to configure SMB via these protocols with an alternate port.
Configuration via GPO
A new Group Policy setting has been introduced to centralize SMB port management. This setting is located in the following path and is known as Alternative Port Mappings.
Computer Configuration => Policies => Administrative Templates => Network => LanMan Workstation
Enabling this policy will allow you to import mappings, including new ports, into the Alternative Port Registry Mappings. For the example provided, you need to enter:
filer.contoso.com:tcp:487
Each entry contains the server name, transfer type, and port number, separated by two dots. Unlike the New-SmbMapping and net.exe commands, there is no need to specify the name of the subscription here.
It is important to check that the SMB server is actively listening on the port of your choice, no matter which port you have chosen.
Alternate port on the server
In this context, “server” refers to any Windows machine that acts as an SMB server, not just Windows Server, but Windows 11 as well. Microsoft offers PowerShell as the only option for configuring a non-standard port. Related orders include:
- Get-SmbServerAlternativePort
- New-SmbServerAlternativePort
- Remove-SmbServerAlternativePort
- Set-SmbServerAlternativePort
The first command displays the configuration of the current active port, while the second command assigns an alternate port to SMB.
New-SmbServerAlternativePort -TransportType QUIC -Port 1111
Currently, the TransportType parameter only supports QUIC, which means that TCP and RDMA can’t have different ports on the server side. Microsoft has likely prioritized SMB over QUIC because the protocol allows direct use over the Internet, which often requires opening different firewall ports. SMB, on the other hand, is usually accessed via a VPN for security reasons. Although it is possible to change the port for all three protocols on the client side, the server only offers the option of setting the QUIC port. This combination may not be useful in practical terms, but it has benefits beyond Windows environments.
For example, Samba allows setting up an alternate port by adding an entry in the smb.conf file, as shown below:
[global]
smb ports = 1445
Choosing a different TCP port on the client can be helpful if the SMB server is behind a load balancer that may not handle SMB traffic on port 445.
Prevent port changes
Administrators can use Group Policy to restrict users from changing ports when mapping a network drive, as this can disrupt connectivity. This policy, called Enable Alternative Ports, is in the following direction:
Computer Configuration => Policies => Administrative Templates => Network => LanMan Workstation.
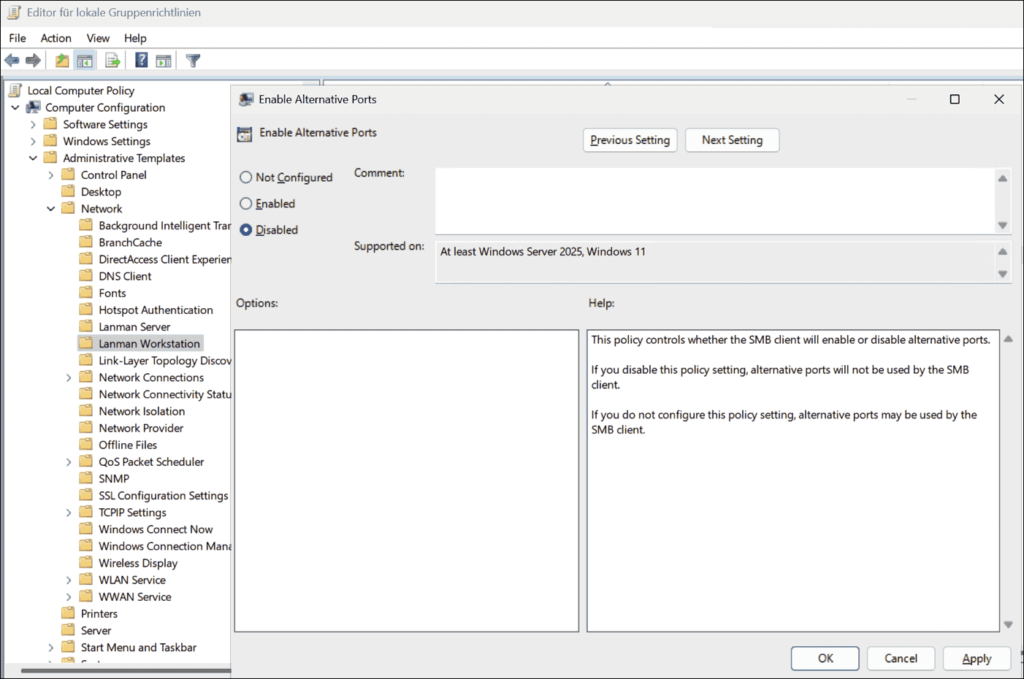
This setting should be disabled to prevent the use of alternative ports. If left unconfigured or enabled, this option will still be available.
Conclusion
Microsoft has upgraded the SMB protocol in Windows Server 2025 with features such as the ability to configure an alternate communication port and remove strict dependencies on TCP 445, the client-side allows the port to be configured for all protocols, while the server only allows configuring the QUIC port. Therefore, the upgraded client-side flexibility is especially useful when you’re dealing with third-party products like a Samba server.
- Design

