Microsoft has announced LiteBox, a new open-source project released under the MIT license that explores an alternative approach to application isolation. Instead of relying on a traditional operating system, LiteBox is built around a sandbox-oriented library operating system model.
Developed in Rust, LiteBox is host-agnostic and designed with a minimal, security-focused operating system surface. Rather than exposing applications to the broad range of system calls, kernel subsystems, and services typical of modern operating systems, LiteBox offers a narrowly defined interface tailored to specific workloads.
The primary objective of the project is to reduce the overall attack surface and limit the potential impact of vulnerabilities in both applications and host systems.
LiteBox follows the library OS architecture, in which core operating system functionality is packaged as libraries that accompany the application itself. This approach allows each workload to operate within its own constrained OS environment, significantly reducing reliance on a large and complex host kernel.
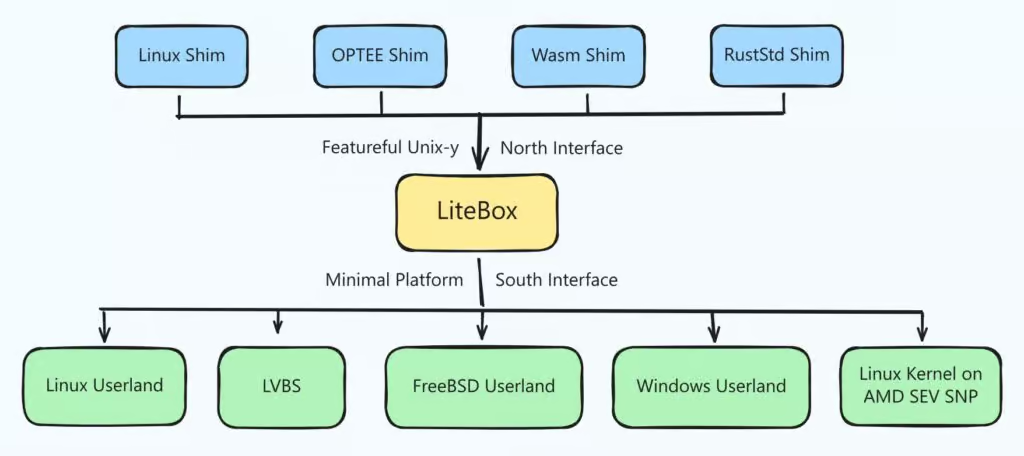
In terms of use cases, LiteBox can sandbox Linux workloads while exposing substantially less kernel functionality than conventional container technologies. On Windows and other supported platforms, it provides a Linux-like execution environment without requiring a full Linux kernel, enabling unmodified Linux applications to run without a complete virtual machine.
The project also supports confidential computing scenarios, including operation on hardware-backed technologies such as AMD SEV-SNP, which provide encrypted memory and reduce trust in the host. Additionally, LiteBox can host OP-TEE workloads on Linux, offering a minimal execution environment for trusted applications.
Target use cases include running untrusted or semi-trusted code, executing user-supplied workloads in cloud environments, supporting CI pipelines, and enabling confidential computing deployments where minimizing the trusted computing base is essential.
Microsoft emphasizes that LiteBox is not intended to replace Linux, Windows, or existing container platforms, nor is it designed for general-purpose or desktop usage. Instead, it serves as a specialized execution layer for tightly controlled workloads requiring predictable behavior and reduced OS exposure.
LiteBox is currently in an early experimental stage, with no stable releases available. Further details and source code can be found on the project’s GitHub repository.