Access Agility WiFi Scanner 2.9.6.557 Free Download
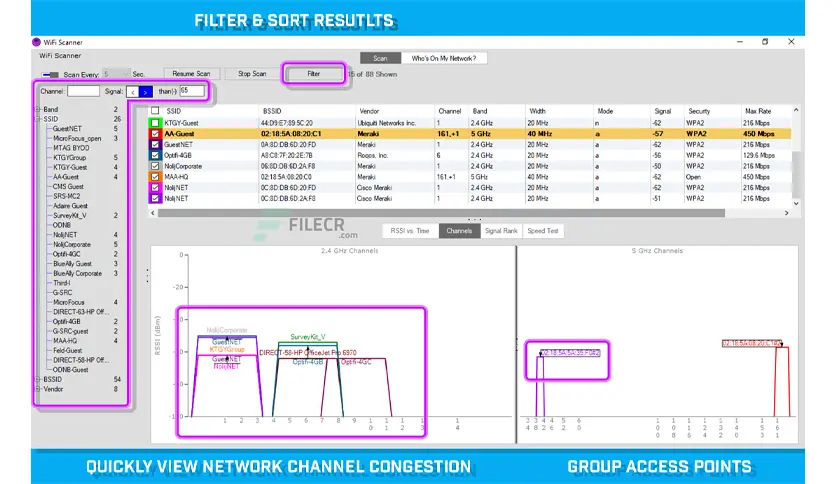
Overview of Access Agility WiFi Scanner Filtering options narrow the results in a high-occupancy area. Choose the networks you want to view by checking/unchecking them as you see fit. The 2.4 and 5 GHz channel graphs allow you to see overlapping and overbearing signal interferences affecting network performance. Speed Test...