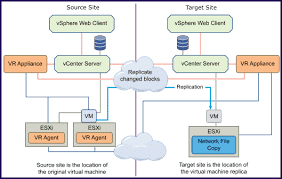
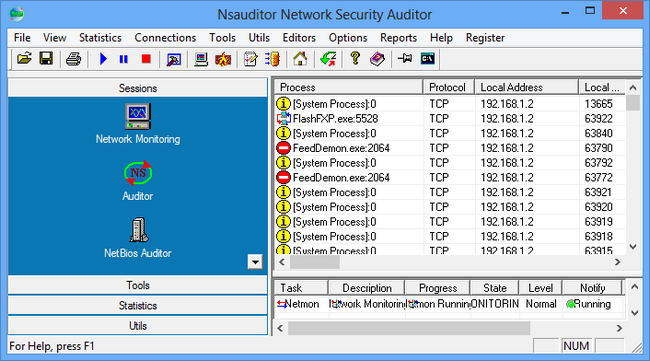
Learn Ethical Hacking & Reverse Engineering
What you'll learn HTML tag information leak Javascript code and function information leak Client code modification vulnerability Javascript code exposure and decryption File redirection vulnerability MDF decryption File extension manipulation exploit Dumpster diving Secure agent browser spoofing Reversing encryption Cracking Steganography, and more... Convert Trial Software to Fully Functional Software...