SSH to Port Other Than 22: How to Do It (with Examples)
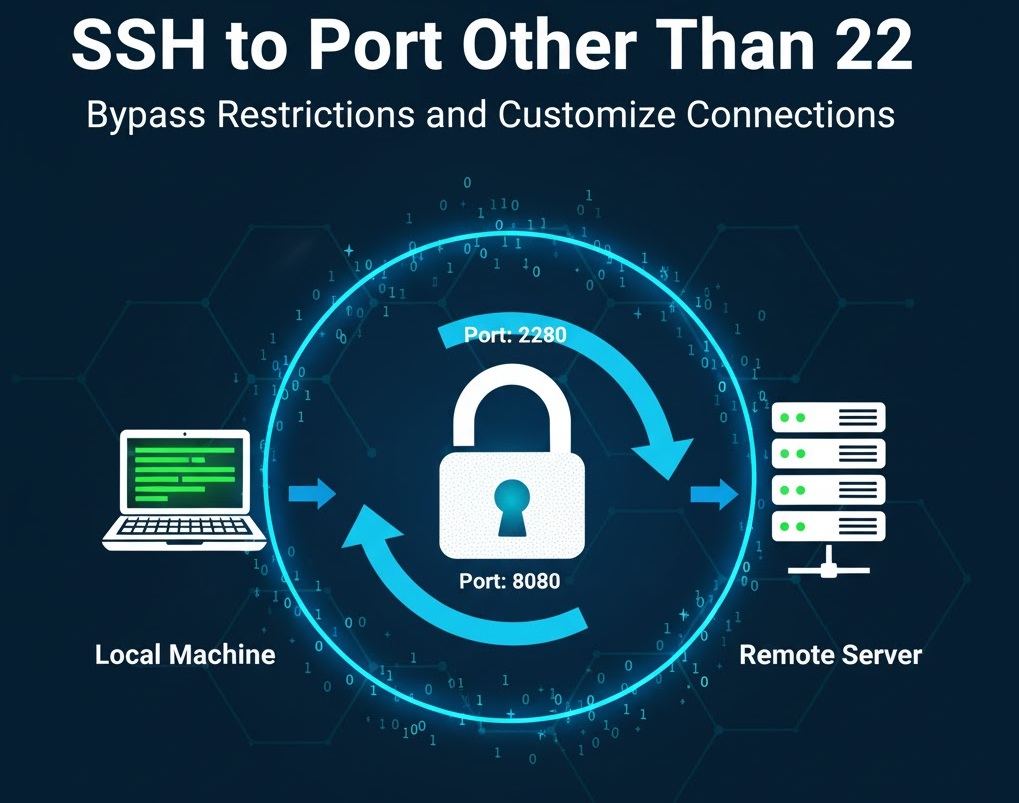
By default, the SSH server runs on port 22. However, there are occasions when it is run in a different port. The -p option can specify the port number to connect to when using the ssh command on Linux. For example, if you want to access a remote server that listens on port 2222, then...