You Might Also Like
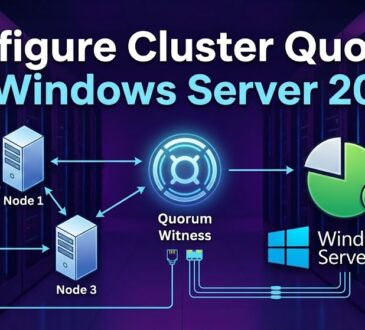
How to Configure Cluster Quorum in Windows Server 2025
253
Understanding Cluster Quorum FundamentalsWhat is Cluster Quorum?The Mathematics of QuorumWhy Witnesses Matter2. Witness Types and Selection CriteriaCloud Witness (Azure Storage)Disk...
KDE Plasma 6.7 Will Offer Instant Light and Dark Mode Switching
Although the Plasma 6.6 desktop has not yet been released (scheduled for February 17), KDE developers have already begun work on version...
Windows Server Infrastructure Microsoft IIS HTTP Web Deploy
270
What you'll learn Windows Server Infrastructure Microsoft IIS IIS HTTP Web Web Deploy Microsoft Infrastructure I am a seasoned IT...
Cybersecurity, Ethical Hacking & Pentesting | All-in-One
289
What you'll learn Learn how to ethically hack and secure real-world systems using tools like Kali Linux, Burp Suite, Metasploit,Nmap and much more.. Master common vulnerabilities such as SQL Injection, XSS, File Upload, SSRF, and Access Control flaws through practical hands-on labs. Perform full penetration testing workflows — from reconnaissance and exploitation to reporting and privilege escalation — in legal, simulated environments. Prepare for real-world certifications and job roles with CTF challenges, Linux/Windows privilege escalation, Bash scripting, and automation techniques. Requirements No prior hacking or cybersecurity experience is required —...