Managing Azure AD Users and Groups
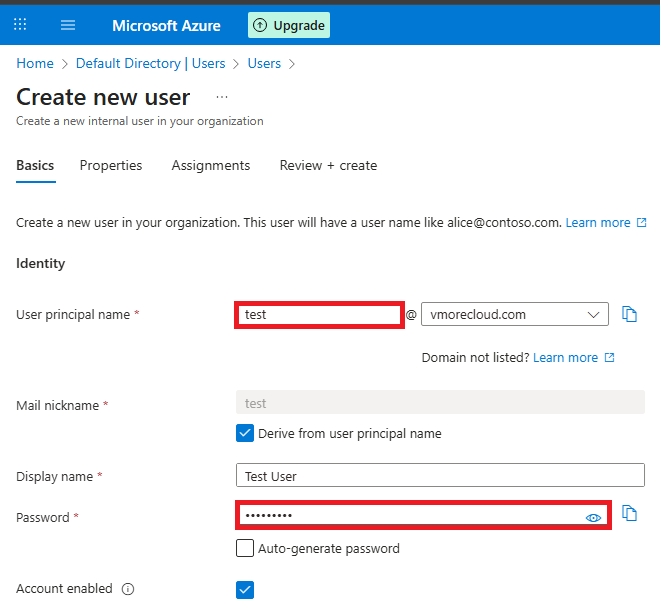
Table of Contents
Managing identities effectively is the backbone of any secure cloud environment. In Microsoft Azure Active Directory (Azure AD), users and groups are at the heart of access management, ensuring that the right people have the right access at the right time. Whether you’re onboarding employees, granting guest access to external partners, or structuring groups for role-based access control (RBAC), Azure AD offers flexible options.
In this blog, we’ll explore:
- What Azure AD users and groups are
- Different types of user accounts (Native, Guest, Service accounts)
- Types of groups and their use cases
- A hands-on lab tutorial to practice in your own Azure subscription
🔑 Understanding Azure AD Users
An Azure AD user represents an individual or identity that can authenticate against Azure resources. Each user has a unique identity in the directory and can be assigned roles, licenses, and group memberships.
Types of User Accounts in Azure AD
Member (Native) User
Created directly in Azure AD or synced from on-premises Active Directory.
- Represents employees or permanent staff in the organization.
- Typically assigned corporate licenses and access to internal resources.
Guest User (B2B Collaboration)
External users are the users who are not part of your AzureAD tenant but have been invited by you. For example, you haveyour active directory domain registered with so any user with anyother domain like username@xyz.com will be a guest user foryou. When you invite any external user, an invitation will be sent to his email ID which is provided by you as a recipient address.This message describes the invitation and has an invitation link to join your tenant.
Service Accounts (Application Users)
- Represent non-human identities such as applications, services, or automation scripts.
- Often used with Azure AD App Registrations and Service Principals.
- Require secure management (passwords, certificates, secrets).
Consumer account
Consumer account Azure AD B2C is a business-to-customer identity provider. This account is been reated under Azure AD B2C. With Azure AD B2C, a user with a third-party identity provider can access Azure applications. The user can access only an Azure AD B2C registered application but cannot access other Azure resources such as the Azure portal. This gets created when the user for the first time logs in to the AD B2C application. But you can also create it manually in Azure AD B2C. The third-party identity providers can be Google, Microsoft, Facebook, and so on.
You can create appropriate users as per your business requirement and can manage them from the Azure AD console.
👥 Understanding Azure AD Groups
Groups in Azure AD help simplify access management by grouping multiple users together. Instead of assigning permissions individually, you assign them to groups.
In the above discussion, we saw the types of users supported in Azure AD. We can have different types of groups also in Azure AD. These groups are defined based on their uses:
You can create this kind of group to manage shared Azure resources access for multiple users. You can assign specific security polices, roles, and so on to specific groups. This makes administrators task easier to manage permissions for multiple users at one place, instead of managing permissions separately for
each user.
Types of Groups in Azure AD
- Security Groups
- Used for managing access to resources.
- Example: Assigning a group to access a SharePoint site or an Azure resource.
- Microsoft 365 Groups (formerly Office 365 Groups)
- Includes collaboration features like shared mailbox, calendar, OneNote, and Planner.
- Example: Project team collaboration with Teams integration.
- Dynamic Groups
- Membership is automatically managed based on rules.
- Example: A dynamic group for all users with “Department = HR”.
⚖️ Best Practices for Managing Users and Groups in Azure AD
- Follow least privilege access by assigning minimal required rights.
- Use Conditional Access policies to secure sign-ins.
- Regularly review group memberships and remove inactive users.
- Apply Privileged Identity Management (PIM) for role-based access control.
- Leverage dynamic groups for automated lifecycle management.
Lab Tutorial: Managing Azure AD Users and Groups
In this lab, we’ll create and manage different types of users and groups in Azure AD.
Step 1: Create a Native User
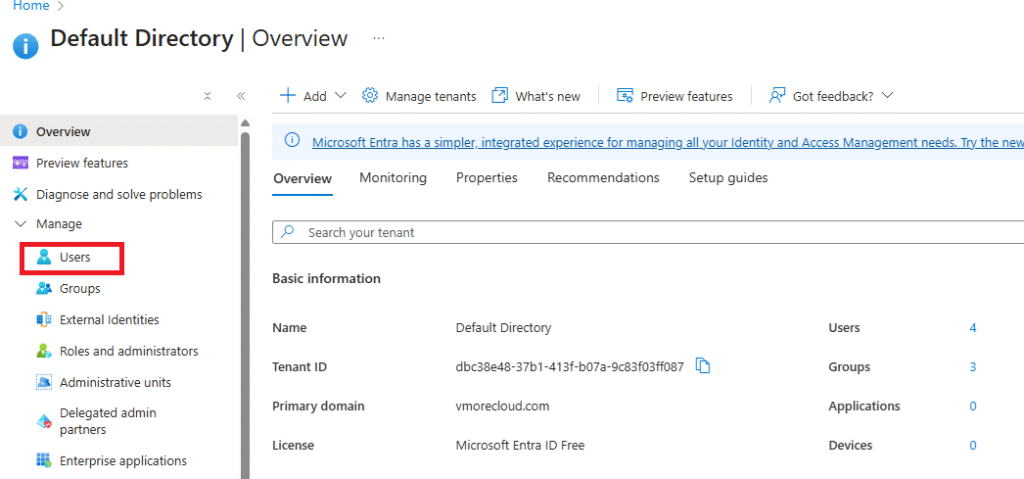
Go to Azure Portal → Azure Active Directory → Users.
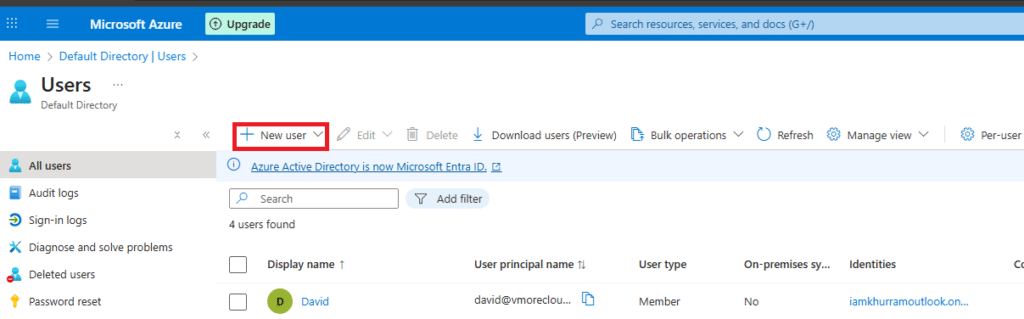
Click + New user → Create user.
Enter a username, password, and assign a role (e.g., User). Even you can choose your desire domain in which you want to register this user. Simply change the domain list and select it. In our case we have chosen our domain vmorecloud.com.

Step 2: Invite a Guest User
In Azure AD → Users, click + New guest user.
Enter the guest’s email (e.g., partner@example.com).
Choose Send invitation → The guest receives an invite email.
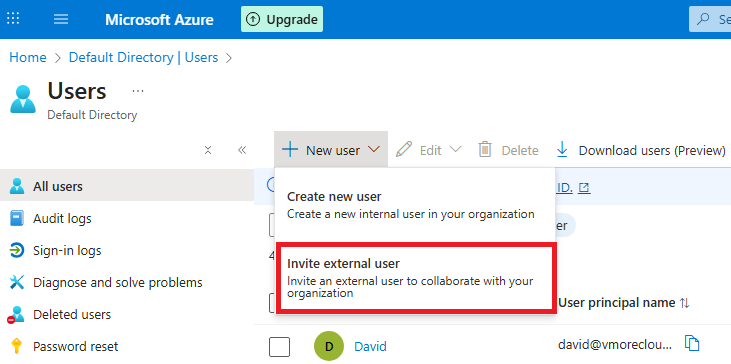
In Azure Active Directory, you can easily invite external users to collaborate by adding them as guest accounts. To do this, navigate to Azure AD → Users and click on + New guest user. Enter the guest’s email address, such as partner@example.com, and then choose Send invitation. Azure AD automatically sends an email invitation to the specified address, allowing the external user to accept and join your directory. Once they accept, their account is added as a Guest User in your tenant. By default, guest users have limited permissions, but you can assign them roles, licenses, or group memberships depending on what resources they need to access. This process is part of Azure AD’s B2B collaboration feature, which enables organizations to securely share apps, files, and services with partners, vendors, or contractors while maintaining full control over access.
Step 3: Create a Security Group
Navigate to Azure AD → Groups → + New group.
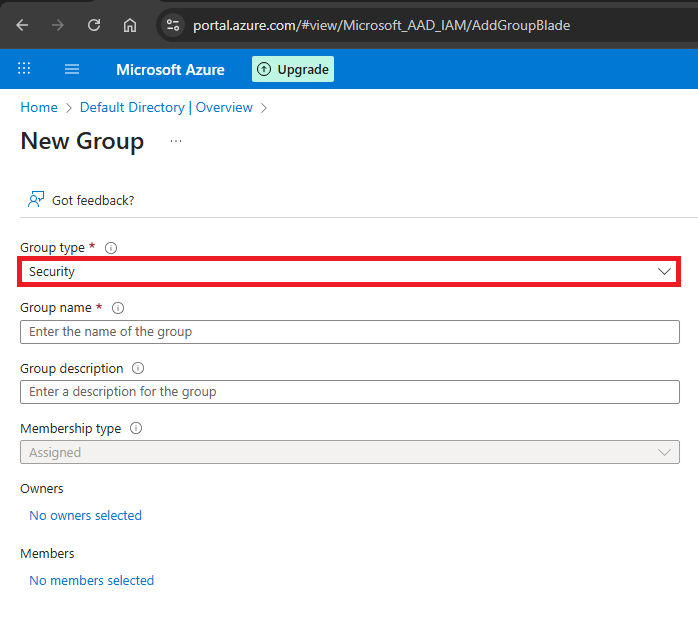
Select Security as the group type.
Add members (Native and Guest users).
Assign this group to a resource (e.g., Storage Account access).
Step 4: Create a Dynamic Group (Optional)
- Go to Azure AD → Groups → + New group.
- Choose Dynamic User as membership type.
- Add a rule, e.g.,
(user.department -eq "HR"). - Save and verify members auto-populate.
🚀 Conclusion
Azure AD simplifies identity and access management by providing flexible user types and group structures. By understanding Native, Guest, and Service accounts, and effectively leveraging Security, Microsoft 365, and Dynamic groups, you can build a secure and efficient access management strategy.
Hands-on labs like the one above are the best way to reinforce your learning and prepare for real-world scenarios.







