Nakivo Backup and Replication – Malware Scan Feature

Totay we’ll talk about malware and how to protect your company from ransomware. NAKIVO Backup & Replication has introduced a powerful Backup Malware Scan feature to ensure that backups remain free from infections before restoration. Imagine you realize that you are infected, your infrastructure shows all signs of ransomware infection (systems not booting, getting corrupted one after another etc..), you would like to restore from backup but how do you know that those backups are clean? You need to scan those backups, to ensure they are clean.
This article explores how this functionality enhances data protection and resilience. If your organization is hit by a ransomware, you aren’t absolutely sure when. As such, when you want to restore, you need to make sure that what you restoring is actually not infected, right?
Think of the malware scan as a pre-recovery scan where the system will first verify that the backup file is clean and then only proceed with restore.
Nakivo Backup Malware Scan:
- Multi-Antivirus Support – Compatible with various antivirus solutions, including Windows Defender, ESET NOD32, Kaspersky, Sophos, and Clam AV
- Ransomware Protection – If malware is detected, the recovery process can be halted or redirected to an isolated network for further analysis
- Flexible Recovery Options – Supports full VM recovery, flash VM boot, physical-to-virtual (P2V) recovery, and universal object recovery
How Nakivo Backup Malware Scan Works?
NAKIVO Backup & Replication connects with supported antivirus tools installed on a Repository Transporter or Scan Server.
Automated Scanning During Recovery – When initiating a recovery job, the system scans the backup for malware before proceeding.
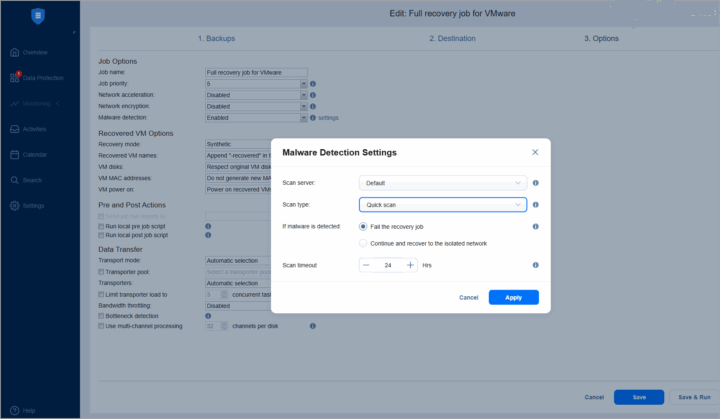
Action on Detection – If malware is found, administrators can choose to:
- Abort the recovery process.
- Restore the infected VM to an isolated network for investigation.
- Apply additional security measures, such as data encryption and immutability.
Malware Scan Advantages?
There are some obvious advantages but there are also necessities for being compliant.
- Regulatory Compliance – Helps organizations meet industry standards for data protection.
- Operational Continuity – Prevents downtime caused by reinfection from compromised backups.
- Enhanced Security – Ensures that backups are free from ransomware and malware before restoration.
Implementing NAKIVO Backup & Replication’s Malware Scan feature requires a few steps to ensure seamless protection for your backups. Here’s how you can set it up:
Step-by-Step Guide to Implementing Backup Malware Scan
- Ensure System Compatibility
- Install NAKIVO Backup & Replication on a supported platform (Windows, Linux, NAS).
- Verify that your Backup Repository Transporter or Scan Server can integrate with antivirus software.
- Install and Configure an Antivirus Solution
- Choose from supported antivirus tools such as Windows Defender, ESET NOD32, Kaspersky, Sophos, or Clam AV.
- Install the antivirus on the Scan Server (or the same server hosting the Backup Repository Transporter).
- Keep virus definition databases updated.
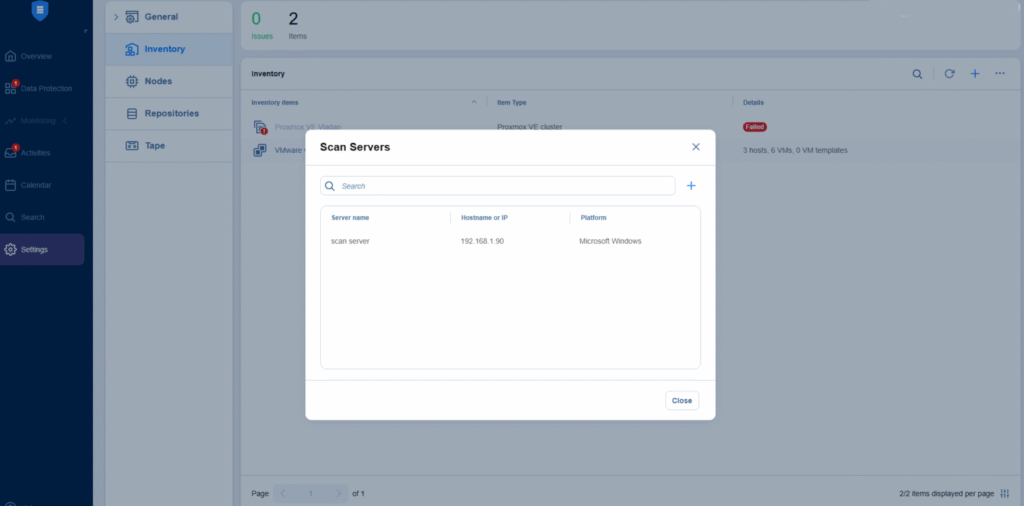
Go to Settings > Inventory > … > Scan servers
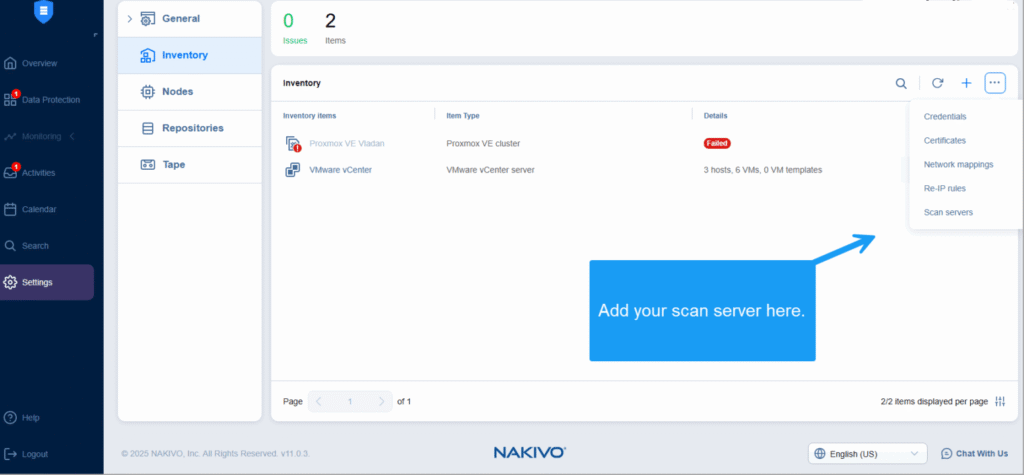
and add your scan server.
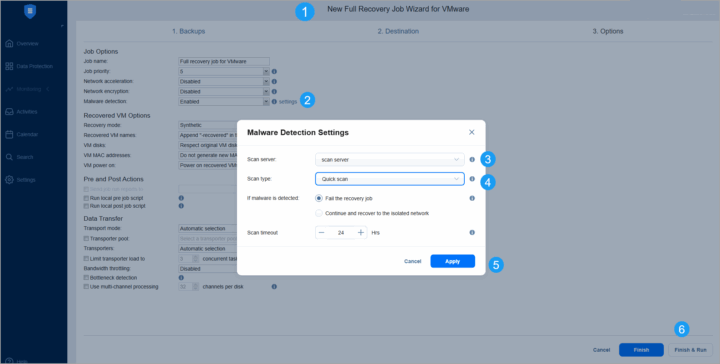
Enable scan when restoring
When creating a restore job, now you can ENABLE the scan, where you need to select your scan server AND scan type.
Best Practices for Secure Backups
- Store critical backups in an air-gapped repository to prevent direct access from infected systems.
- Enable backup encryption for sensitive data.
- Enable immutability on your storage repo.
- Implement role-based access controls (RBAC) to restrict unauthorized modifications.
In case ransomware is detected, the NAKIVO solution can either abort the recovery job or send the infected VM to an isolated network for further investigation.
Check here – Nakivo Malware scan
Trial v11 download here.









