Active Directory Federation Services on Windows Server 2022
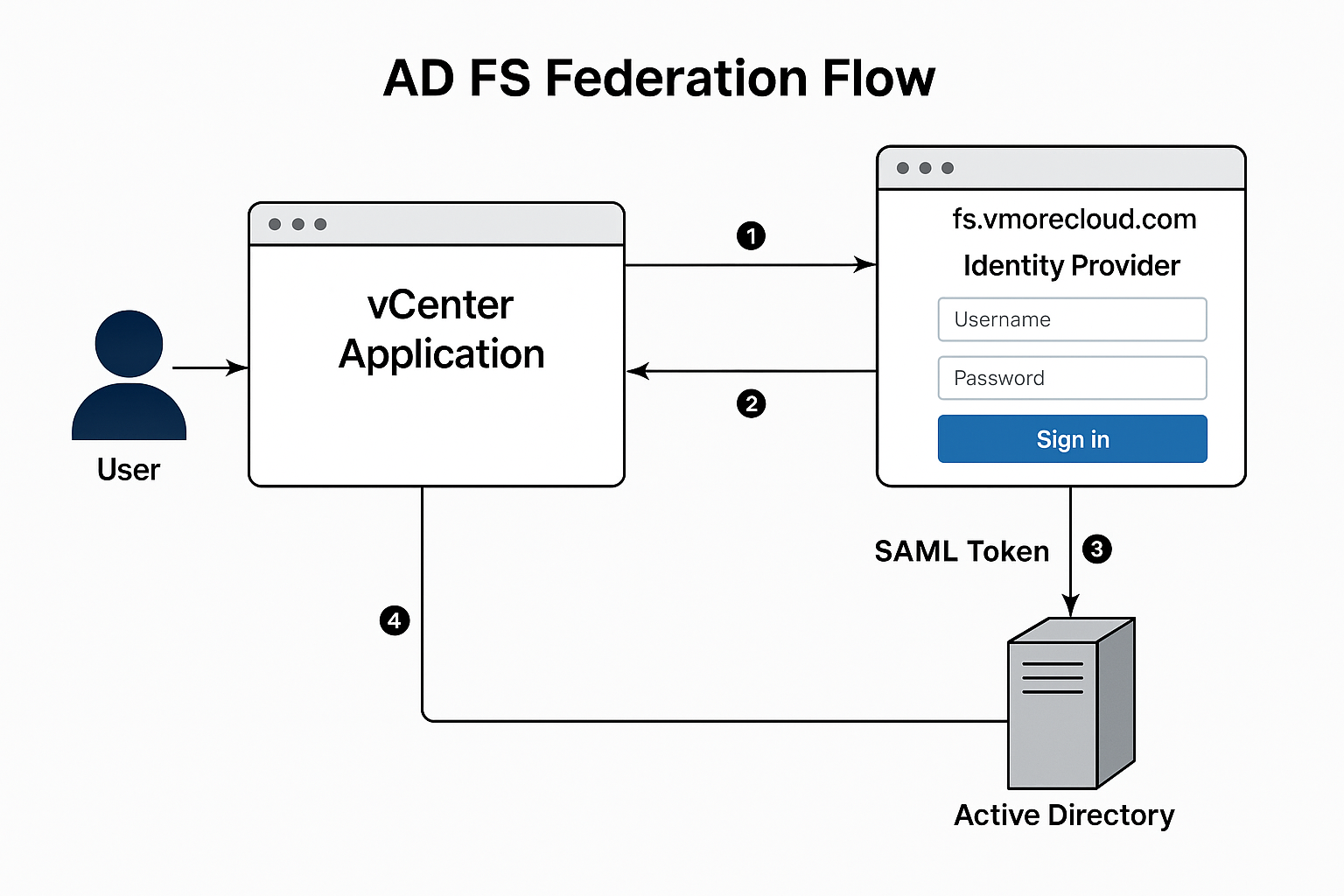
Table of Contents
🔍 What is Active Directory Federation Services (AD FS)?
Active Directory Federation Services (AD FS) is a Microsoft identity access solution that enables Single Sign-On (SSO) across multiple applications, systems, and even organizations. AD FS allows users to securely access resources using a single set of credentials whether those resources are hosted on-premises or in the cloud.
By leveraging claims-based authentication, AD FS supports federated identity, which means it can establish trust between different domains or identity systems perfect for hybrid cloud setups, third-party services, and applications like VMware vCenter, Microsoft 365, and Salesforce.
🎯 Why Use AD FS?
In today’s multi-cloud, hybrid IT landscape, managing authentication securely and efficiently is more critical than ever. Here’s why AD FS matters:
- ✅ Centralized Identity: Users log in once and gain access to multiple systems.
- 🔐 Stronger Security: Supports Multi-Factor Authentication (MFA) and smartcards.
- 🌐 Federation Ready: Bridges trust between your Active Directory domain and external applications/services.
- 🧩 SAML & OAuth Support: Integrates with modern protocols for cloud and web apps.
🏗️ Lab Setup: What You Need
- Windows Server 2022 (Installed and joined to vmorecloud.com)
- Domain Admin privileges
- SSL Certificate (Trusted and configured for fs.vmorecloud.com)
- Static IP assigned
- DNS A Record for fs.vmorecloud.com pointing to your AD FS server
🛠️ How to Install and Configure AD FS on Windows Server 2022
To install the Active Directory Federation Services (AD FS) role on your Windows Server 2022 system, follow this step-by-step process. AD FS is essential for enabling secure identity federation and Single Sign-On (SSO) capabilities between your internal Active Directory and trusted external systems, such as VMware vCenter, Microsoft 365, and cloud services.
Let’s walk through setting up AD FS in a real-world lab environment using Windows Server 2022.
Click Here to install Windows Server 2022
🔹 Step 1: Install the AD FS Role
Launch Server Manager
Start by opening Server Manager from the Start menu or by searching for it in the taskbar. Server Manager is your central console for managing roles, features, and system configuration.
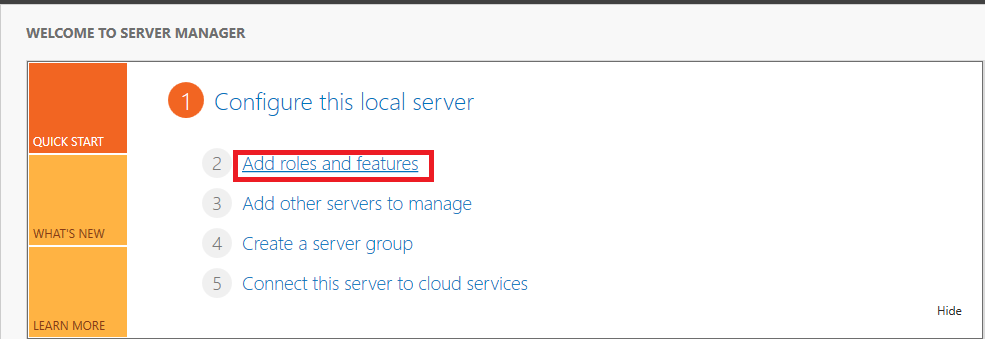
Click on Manage → Add Roles and Features
In the top-right corner of Server Manager, click Manage and select Add Roles and Features to launch the installation wizard.
Proceed through the Installation Wizard
Click Next through the following screens:
- Before You Begin
- Installation Type (select Role-based or feature-based installation)
- Server Selection (choose the local server or appropriate remote server)
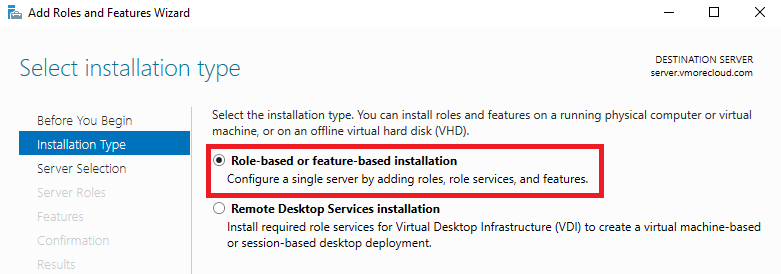
4. Select the AD FS Role
When you reach the Server Roles page:
Scroll down and check Active Directory Federation Services. A prompt may appear to install required features. Click Add Features, then click Next.
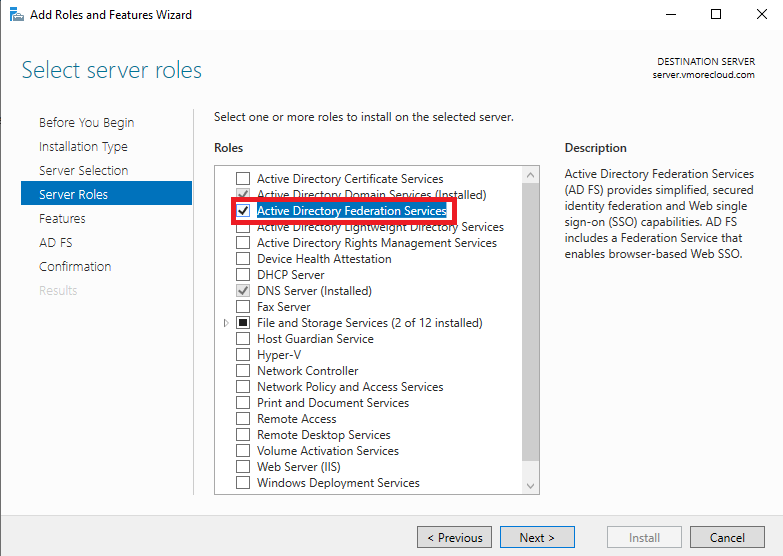
5. Complete the Wizard and Install
Proceed through the Features and AD FS Introduction pages by clicking Next. On the Confirmation page, click Install to begin the installation process.
Once installation completes, you’ll be ready to move forward with the AD FS Configuration Wizard, where you’ll set up your federation service.
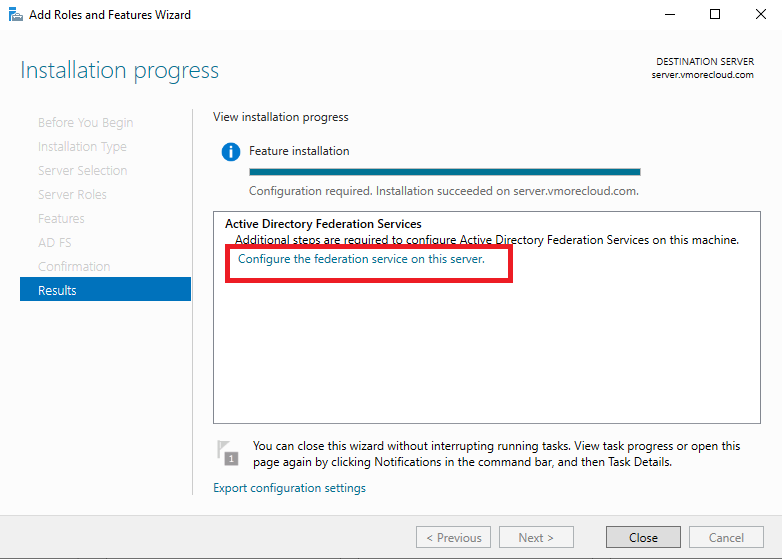
This setup is the foundation for enabling identity federation across platforms like vCenter using SAML, providing secure and seamless user authentication.
🔹 Step 2: Configure AD FS
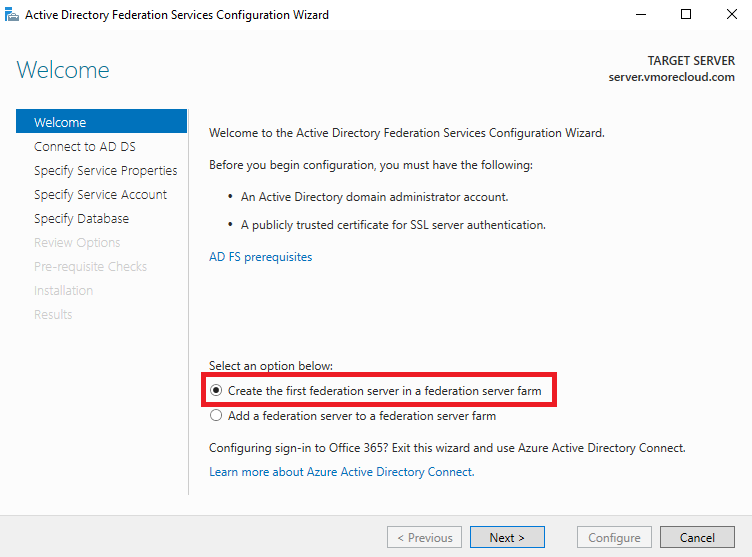
In the AD FS Configuration Wizard, select:
Create the first federation server in a federation server farm
Enter your domain admin credentials when prompted.
Get an SSL Certificate
AD FS requires an SSL certificate (HTTPS) for the Federation Service. You have two options:
Option 1: Use a Public SSL Certificate (Recommended for production)
Get an SSL cert for adfs.vmorecloud.com from a provider like Let’s Encrypt, GoDaddy, etc.
You’ll need to:
Set up a DNS record for adfs.vmorecloud.com → point to your server’s IP.
Install the certificate on your server (import it into Local Computer > Personal store).
Option 2: Use a Self-Signed Certificate (Only for testing!)
Open PowerShell and run:
New-SelfSignedCertificate `
-DnsName "adfs.vmorecloud.com" `
-CertStoreLocation "cert:\LocalMachine\My" `
-KeyExportPolicy Exportable `
-FriendlyName "ADFS Test Cert" `
-NotAfter (Get-Date).AddYears(1)
This creates a 1-year cert in the Local Machine > Personal store. Replace “admin@123” with your own secure password.
Now export it.
$password = ConvertTo-SecureString -String "admin@123" -Force -AsPlainText
Export-PfxCertificate -Cert $cert `
-FilePath "C:\cert\adfs-cert.pfx" `
-Password $password
For SSL certificate:
Select your installed certificate for fs.vmorecloud.com.
Set the Federation Service Name (same as your certificate FQDN).
Set a Display Name (e.g., vMoreCloud Identity Provider).
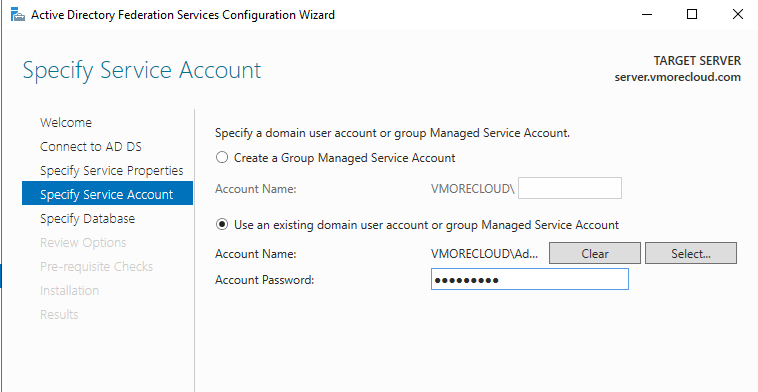
Choose a Group Managed Service Account (gMSA) or specify a domain user.
Click Next, review, and configure.
Step 3: Configure AD FS
After install, click “Configure the federation service…”
Choose:
Create the first federation server in a federation farm
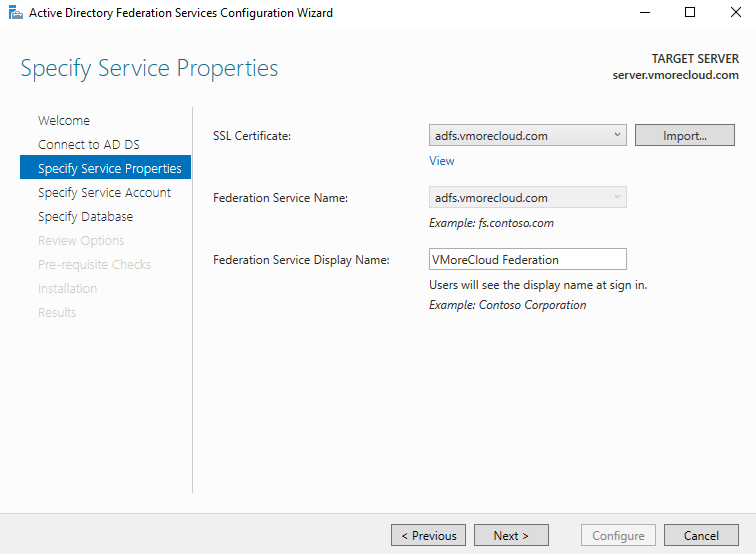
Select the SSL certificate (adfs.vmorecloud.com)
Federation Service Name: adfs.vmorecloud.com
Federation Display Name: Something like “VMoreCloud Federation”
Use a domain admin account to continue
Finish the setup
https://adfs.vmorecloud.com/adfs/ls/idpinitiatedsignon
🔹 Step 3: Verify AD FS Installation
Open a browser and navigate to:
https://fs.vmorecloud.com/adfs/ls/IdpInitiatedSignon.aspx. You should see a Sign In page. Log in using your domain credentials.
🎉 If successful, AD FS is working and ready for federation tasks.
🔗 Step 4: Optional – Configure AD FS for SAML Applications
You can now integrate AD FS with third-party applications (like vCenter, AWS, or Microsoft 365) using SAML 2.0.
- Open AD FS Management Console.
- Go to Relying Party Trusts → Add Relying Party Trust.
- Use the wizard to specify:
- SAML endpoints
- Token signing certificate
- Claims rules (e.g.,
NameID,Email,Group)
🔐 Be sure to define claims rules using the Claim Rule Wizard for proper identity mapping.
⚙️ Managing AD FS Post-Deployment
- Enable MFA using Conditional Access Policies.
- Configure Token Lifetimes for enhanced security.
- Monitor audit logs and Event Viewer for troubleshooting.
- Use PowerShell (Get-AdfsRelyingPartyTrust) for automation and scripting.
🔄 Summary: Why AD FS is a Must-Have in 2025
AD FS continues to be a critical part of identity strategy in modern IT environments:
- Supports hybrid Active Directory scenarios.
- Integrates seamlessly with VMware, Microsoft, and third-party SSO providers.
- Gives enterprises complete control over authentication, federation, and security policies.
If you’ve deployed Windows Server 2022 and are looking to extend authentication across platforms AD FS should be a foundational element of your architecture.
Final Thoughts
With AD FS on Windows Server 2022, you gain a secure, reliable, and flexible way to extend authentication beyond your local domain. Whether you’re integrating VMware vCenter, building a hybrid cloud, or simply want seamless access across apps this guide helps you get started the right way.








